Hacker involved in stealing of $11m from Nigerian companies, others arrested
)
Authorities in the West African country of Ivory Coast have arrested a suspected senior member of a cybercrime syndicate, code-named OPERA1ER, that stole an estimated sum of $11 million from companies in Nigeria, the Republic of Benin, Cameroon, 11 other African countries, and Argentina.
The arrest was made following concerted efforts involving African Joint Operation against Cybercrime (AFJOC) and the INTERPOL Support Programme for the African Union (ISPA), in conjunction with AFRIPOL, the Direction de L'information et des Traces Technologiques (DITT), Group-IB and the Orange CERT Coordination Center (Orange-CERT-CC).
In an attempt to disrupt the operations of the cybercriminal syndicate, Group-IB’s Threat Intelligence team alongside its partners, Orange-CERT-CC, started tracking the activities of OPERA1ER in 2019.
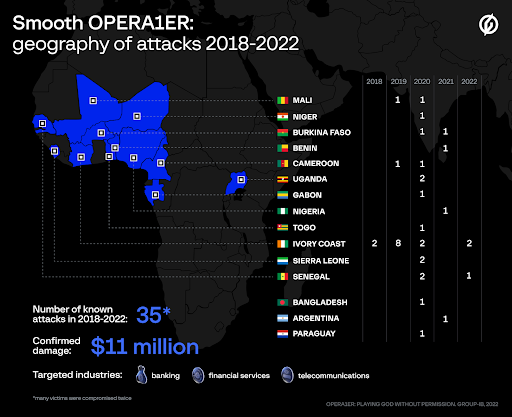
A November 2022 report by the two bodies detailed financially motivated attacks from a prolific Francophone threat actor, codenamed OPERA1ER.
The group managed to carry out more than 30 successful attacks against financial institutions, banks, mobile banking services, and telecommunications companies in Côte d'Ivoire, Mali, Burkina Faso, Benin, Cameroon, Bangladesh, Gabon, Niger, Nigeria, Paraguay, Senegal, Sierra Leone, Uganda, Togo, and Argentina between March 2018 and October 2022.
OPERA1ER was confirmed to have stolen at least $11 million from their attacks, although the actual damages could be as high as $30 million. Group-IB provided threat intelligence and notifications to the affected companies during the investigation, helping to reduce financial losses.
How the suspect was arrested
In a report sent to this writer by Group-IB on Wednesday, July 5, 2023, the cybersecurity firm disclosed how an INTERPOL-led effort dubbed Operation Nervone led to the arrest of a key figure of the syndicate.
Group-IB’s Threat Intelligence and High-Tech Crime Investigations teams contributed to Operation Nervone by sharing, in collaboration with Orange-CERT-CC, information on OPERA1ER; identifying the attackers’ infrastructure, analysing their digital traces and assembling data that uncovered the identity and potential location of a key figure in the organisation.
Leveraging the supplied intelligence, the suspect was subsequently detained in Abidjan, the capital of Ivory Coast. The operation also benefited from the efforts of law enforcement and governmental agencies from several INTERPOL member states.
“We have been tracking OPERA1ER since 2019. Any attempt to investigate a sophisticated threat actor such as OPERA1ER, which stole millions from financial service companies and telecom providers across the world, requires a highly coordinated effort between public and private sector bodies," Dmitry Volkov, CEO at Group-IB, said.
Speaking further, Volkov said, "The success of Operation Nervone exemplifies the importance of threat data exchange, and thanks to our collaboration with INTERPOL, Orange-CERT-CC and private and public sector partners, we were collectively able to piece together the whole puzzle."
)
)
)
)
)
)
)
)